Post-Quantum Secure Communication for the Enterprise
Future-proof your data with end-to-end encrypted messaging and file-sharing built on NIST-approved post-quantum cryptography.

Quantum Cybersecurity Solutions
Innovative strategies for protecting digital assets with quantum technology.


Identify vulnerabilities and enhance your security posture with quantum insights.
Advanced Threat Detection
Utilize quantum algorithms to detect and respond to cyber threats in real-time.
Secure Data Encryption
Stay Ahead in Cybersecurity
Join us for quantum-powered digital defense insights.

Quick Highlights
⚡ Quantum-Resilient
Built on Kyber, Dilithium, and Falcon
Qsafe delivers quantum-resilient cybersecurity powered by Kyber, Dilithium, and Falcon algorithms. Our solutions protect data and communications against emerging quantum threats, ensuring businesses stay secure in the quantum era.


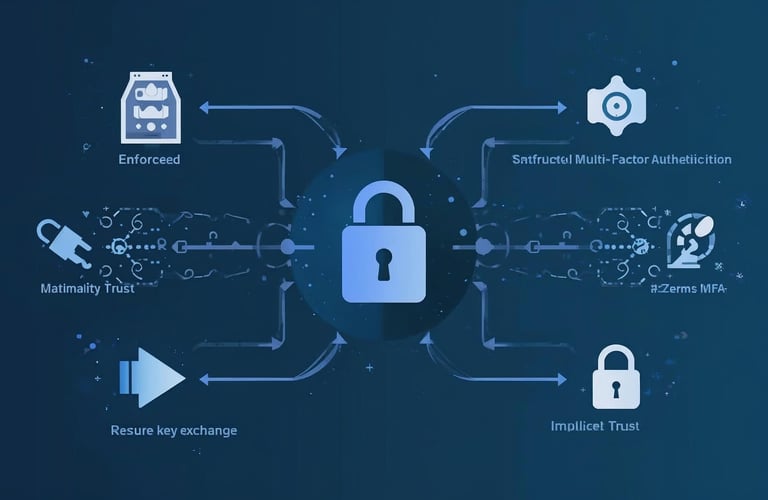
🔐 Zero-Trust Architecture
Enforced MFA, secure key exchange, no implicit trust
Qsafe implements a zero-trust architecture, enforcing multi-factor authentication, secure key exchanges, and eliminating implicit trust. This ensures every access request is verified, keeping your data and systems fully protected.
☁️ Cloud Integration
Connects with Google Drive, Outlook, OneDrive
Qsafe offers seamless cloud integration, connecting effortlessly with Google Drive, Outlook, and OneDrive. This enables secure access and protection of your data across all major platforms.


Quantum Defense
Explore innovative solutions at the intersection of quantum computing.












© 2025. All rights reserved.




